Cyber security is the state or process of protecting and recovery computer systems, networks, devices and programs from any type of cyber attack. Cyber attacks are becoming an evolving danger to the sensitive data of organizations, their employees and individuals.
As the world becomes increasingly reliant on the Internet and computer systems and the next generation of smart Internet of Things enabled devices with access to wireless networks via Bluetooth and Wi-Fi come online, the average level of every organization’s cyber security risks and cybercrime is on the rise.
Businesses and nation states have begun to recognize Cybersecurity as a major challenge due to its complexity

What types of cyber security threats are there?
The process of keeping up with new technologies, security trends and threat intelligence is a massive task. The first stage is to understand what information may be valuable to an outside party and then how they may gain access to it.
Below we have outlined the common sources of cyber threats that you should be aware of.
What is a backdoor?
A backdoor is a method of bypassing normal authentication or encryption in a computer system, product, or embedded device (like a router). Cyber attackers often use backdoors to to secure remote access to a computer, obtain access to plaintext passports, delete hard drives, or transfer information within the cloud.
A backdoor can also take the form of a hidden part of a program, a separate program, code in firmware of hardware or operating systems. Although some backdoors are secretly installed, other backdoors are deliberate and known. These have legitimate uses such as providing the manufacturer with a way to reset a user’s password.
These legitimate backdoors can result in data leaks when misconfigured resulting in access to sensitive data and personal information that may be used for identity theft.
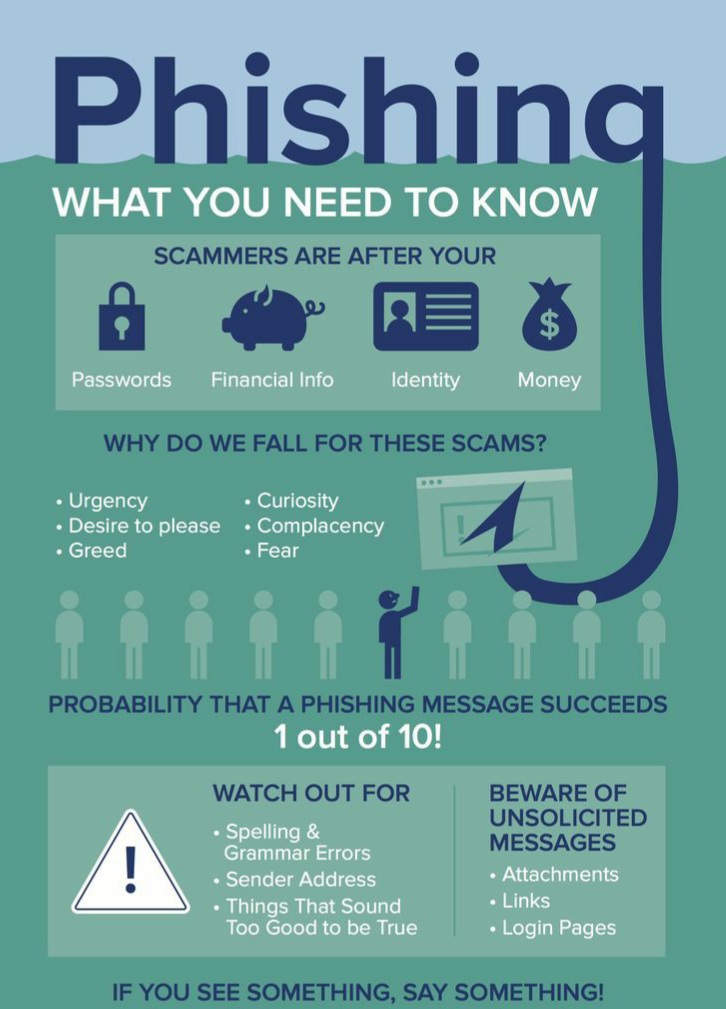
What is phishing?
Phishing is an attempt to acquire sensitive information such as usernames, passwords or credit cards directly from the end-user.
A typical phishing scam occurs through email spoofing or text messaging that directs the user to urgently enter their details into a fake website that looks and feels identical to the legitimate website. Once the user submits their details, their credentials are used to gain access to their real account.
Phishing is largely an attack on the end-user rather than technology, meaning education is an important cybersecurity measure that reduces the security risk of passwords being phished.
Measures To Enhance Cybersecurity
What is two factor authentication?
1) Two factor authentication is a method of mitigating unauthorized access to a system or sensitive information. The idea is that the user “needs to know something” like their username or password and has “to have something” like a card, dongle, cellphone, or app.
Training is often involved to mitigate social engineering risk but even in highly disciplined environments social engineering attacks are difficult to prevent.
Two factor authentication improves security and reduces the impact of phishing and other social engineering attacks as an attacker needs credentials and the two factor authentication method to gain access.
- Drive locks: software tools that encrypt hard drives
- Disabling USB ports: prevents unauthorized access to an otherwise secure computer
- Mobile phones: built-in capabilities like Bluetooth, Bluetooth low energy (LE), Near field communication (NFC) and biometric validation offer new secure ways to connect to access control systems like access to secure buildings

2. Use a full-service internet security suite
3. Use strong passwords
Don’t repeat your passwords on different sites, and change your passwords regularly. Make them complex. That means using a combination of at least 10 letters, numbers, and symbols. A password management application can help you to keep your passwords locked down.
4. Keep your software updated
This is especially important with your operating systems and internet security software. Cybercriminals frequently use known exploits, or flaws, in your software to gain access to your system. Patching those exploits and flaws can make it less likely that you’ll become a cybercrime target.
5. Manage your social media settings

Leave a comment